Can't beat OAuth2.
Let's learn open authorization(OAuth) in 2 mins. No prior knowledge needed
Before starting let's keep these things in mind about OAuth:
- Stands for Open Authorization (GO FOSS!)
- This a high level introduction, future part will cover implementation and in-depth information
- Used for Authorization and not authentication (there is a catch tho!)
- It is not our lord and savior but it solves a lot of things for us
- It does have security concerns
Why do we need it?
Keeping it very short! To best understand the need of such a protocol we should look at how it helps us in our daily internet lives.
Imagine visiting a website that requires credentials before you can access its wonderful services (I see you, Chegg!). You go to their login page only to find that it asks for your email address and password. If you're like me, you'd be pissed by this absurdity. But then you spot those oddly shaped buttons at the bottom. Upon closer inspection, you realize they feature familiar faces, and you actually have accounts with some of them. After a few clicks, voila! you’re in the website and can go about your day. All this couldn't have had happened without our darling OAuth protocol 🥂.
Authorization is not authentication
At this point, you might have got some idea about OAuth. I would like to make it clear that OAuth is not an authentication technique it is an authorization technique. You might need to authenticate yourself to grant the necessary permissions but OAuth as a protocol does not care about authentication. To understand the difference between authentication and authorization, consider what questions they ask individually.
- Authentication - Who is it ?
- Authorization - What can they access?
- Together they question - Who is it and what can they access?
So, Oauth just questions the "What" part of our security equation. "Who" part is a by-product and doesn't gurantee security by any means.
"Why do I need so many paasswordss! Can't it be simpler. Anyways my password is ..."
How does it work?
To explain in simple terms, we will take an example of the classic cryptography duo, Alice and Bob. Let's say Alice wants to view Bob's progress in the gym and decides to ask the gym for this information. It is important that the gym knows whether Alice is allowed to view the progress data. To tackle this, Bob can ask the gym to assign Alice a token that will serve as a testament to the fact that Bob has allowed Alice to view specific data on his behalf. For all my visual learners, Take a look at the image below.
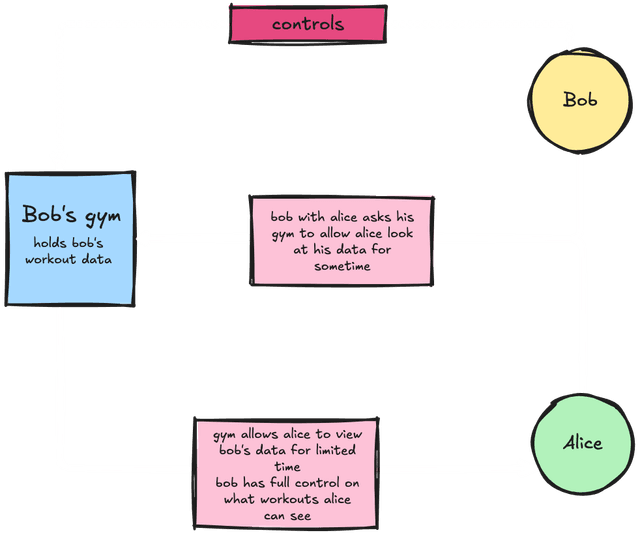
I hope the image does help you with your understanding of this protocol. I would also like to share a more techy diagram for this concept which we will discuss and explain in the next part.
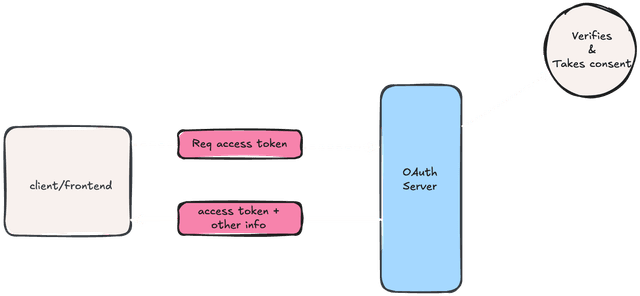
NOTE : OAuth protocol is infamous for being complex and confusing, while that discussion does have some weight, our focus on this technology for this part of blog, mainly revolves around its abstractions.
Next part....
I would love to go over the code implementation of OAuth in 2 mins. We will see what our sample request and response contains. My choice would be a javascript based auth library, authjs.dev . It makes OAuth insanely simple and intuitive. I will update the link to second part here, untill then See ya!